
Third-Party Risk Management Framework
Today’s third parties require more access to data assets of organizations they do business with and are increasingly working with their own third parties (also known as Nth or Fourth Parties), multiplying the size and complexity of the third-party network. In fact, in the last four years, legal and compliance leaders have classified 2.5X more third parties as high-risk. Gartner’s study on Third-party risk, reveals that twice as many compliance leaders identify third-party risk as a top threat. This is because third-party risks have fundamentally changed. Leaders say they have experienced:
- Greater variability in the maturity of their third-party network.
- Third parties work with an increasing number of third parties themselves.
- Increased third-party access to organizational data assets.
More than 4,100 publicly disclosed data breaches occurred in 2022 exposing approximately 22 billion records (reported by Security Magazine). Every third party an organization is engaging, they must consider various associated third-party risks, including financial risks, reputation, resiliency, information security, cyber security exposures, legal actions or compliance, and performance failures that could ultimately disrupt their organization. Building a comprehensive TPRM Framework is increasingly important as organizations outsource more significant portions of their workloads to third-party suppliers.
Introduction to TPRM frameworks:
Third-party risk management (TPRM) frameworks provide organizations with a roadmap to build their TPRM programs based on industry-standard best practices. Frameworks the foundation of TPRM programs and provide the cornerstone of baseline control requirements for third-party vendors and suppliers.
There is no single approach to developing a TPRM framework, but some commonly used frameworks provide a solid starting point. Frameworks provided by organizations such as the National Institute of Standards and Technology (NIST) and the International Standards Organization (ISO) are a great place to start.
Third-party risk management policies guide organizations in the building, applying, managing, and implementing best practices. When implementing a third-party risk management framework, companies must examine the nature of the risk involved and deal with the changing business, regulatory and legal environments – and their potential impact on the organization’s operation. Effectively utilizing TPRM frameworks will reduce risks to organizations and their customers.
TPRM framework for an organization:
No single framework is likely to provide every organization with every control to comprehensively meet disparate regulatory, risk management, and due diligence objectives and requirements. Many organizations choose to work exclusively with NIST or ISO and draw from multiple frameworks and guidance documents from each of those bodies when developing and maturing their programs.
The following considerations and how they impact your organization are important when selecting a TPRM framework. Understanding the organizational risks is the first step in choosing the proper framework for your company. The infographic below illustrates many of the relevant risk categories
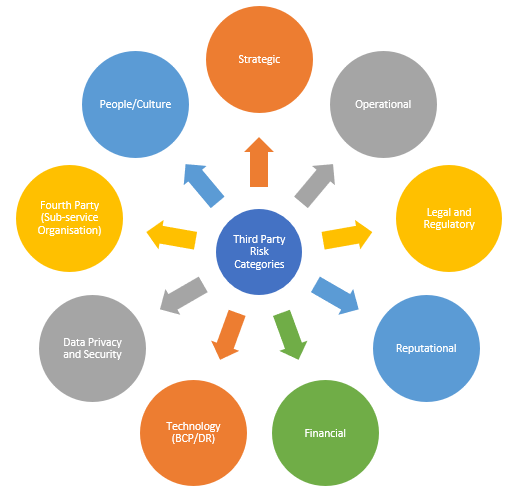
Some vendors or third parties may push back or be reluctant to engage in the assessment of their risk and security posture due to the time, and resources sometimes necessary to satisfy. TPRM isn’t just about ensuring that a partnership does not expose your organization to intolerable risk potential; it is also about rewarding vendors that reduce your organization’s risks through best practices. That’s why it’s important to select the correct TPRM framework and understand its impact on your ecosystem of external vendors.
Aspects that need to be considered to help you build a TPRM Framework:
- Does the framework enable automation for data gathering?
- How does the framework integrate with your existing workflows?
- Does the framework have or publish available benchmarks?
- How often is the framework updated to address changing levels of risk such as cybersecurity risk, geo-political changes, and changes in the legal environment?
- Are there standard definitions of High, Moderate, and Low risk?
- What TPRM frameworks do your customers use and require you to respond to?
- Are there standard remediation processes in the literature associated with the TPRM framework?
- Are there specific regulatory requirements that need to be considered? (HIPAA, CCPA, BSA, GLBA, etc.,)
- How broadly is the TPRM Framework adopted? i.e., can it be used to address fourth-party risk concerns?
Understanding the specific business requirements or the risk environment in which the business operates will help an organization build a mature and effective TPRM Framework. Shared Assessments, NIST 800-161, and ISO 27036 can provide specific examples of important SCRM (Supply Chain Risk Management) and TPRM controls, while organizations such as ISACA are valuable knowledge sources of practically applied best practice, third-party risk management processes.
About Author:

Narayanan Rajendran is a Management Consultant and Leads Third Party Risk Managed Services at Templar Shield. He has 15+ years of progressive experience advising global majors/Fortune 500 companies on Governance, Risk Management, and Compliance initiatives.

